
WordPress Brute Force Attacks – How to Protect Your Website
WordPress brute force attacks are a complex matter. Brute-forcing is one of the first, most primitive types of cyber-attacks. That is due to its availability of integration versus all types of websites and platforms. Over time, the progression of a website’s usage complexity has given the birth of other, more advanced attacks.
However, the first types of attacks has always been the most basic. So basic that they can be applied to a mass number of situations, such as the brute force approach.
What Exactly is a WordPress Brute Force Attack?
When it comes to cybersecurity, there are all sorts of malicious attacks. One may use them to engage in getting past the security of your WordPress website. One of those malicious attacks controversially is an attempt of guessing a username/password combination. This is done via “brute force attacks” which action we call “brute forcing.”
This attack type is not native only to WordPress but happens with all the web apps out there. However, since WordPress is popular, it’s a frequent target.
How Effective and Dangerous Is the WordPress Brute Force Attack?
A common misconception about brute-forcing is that people consider it to be an effective method of obtaining control over one’s website, while in reality, the chance of success of such an attack towards a website with a moderately secure password is slim to none.
The attack itself is quite widespread in terms of occurrences due to its popularity and mass availability, which comes from the fact that it is simply easy to set up. However, without the exact knowledge of what you are doing most such attacks have the destiny of failure.
What Does the Attack Include?
A WordPress brute force attack consists of a predefined “wordlist” of username(s) and passwords combined into one text file. This file is then also combined with various types of different programs/software towards the login form fields of your website, or through any file, your application may have that accept user login data in attempts to find a possible match.
What Can We Do Towards Preventing a WordPress Brute Force Attack?
Prerequisite: Create a Strong Complex Password
The most common ways of protecting against such an attack are honestly the most effective as well. To put it simply, if your password is not in the attackers’ wordlist, they can’t get in. These wordlists usually consist of: dictionary words, random letters/number combinations, phrases, expressions, common names, countries, towns, and basically anything you can think of that isn’t absolutely random.
While we would never recommend a password generator, because even though they are based upon some algorithm of creation, dragging my hand through the keyboard will always create an impenetrable password.
On a technical level: Strong Server Protection
On a server level, all of our servers come with pre-installed Firewalls, WAF, BitNinja, and other top-quality security protocols which will mitigate nearly 80% of all attack attempts before they even start. Learn more about how FastGuard protects your website and the technologies we use
For those who do get past the initial defense, we suggest arranging the following security reinforcements:
Whitelist IP Address
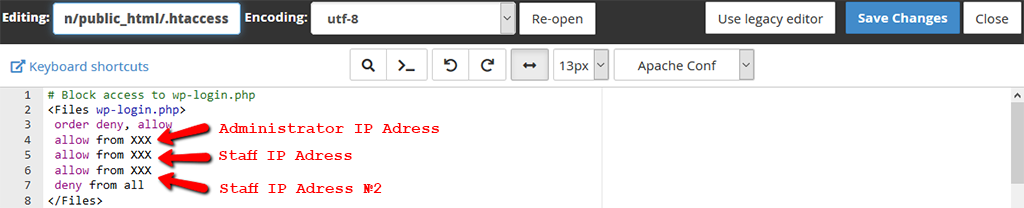
If you would like to cut off any chance a hacker may have of getting a glimpse of the insides of your WordPress dashboard, it’s about time to limit the access to the administrator and his staff only, you can do this by creating or modifying your existing .htaccess file by adding the following code to it:
# Block access to wp-login.php
<Files wp-login.php>
order deny, allow
allow from XXX
allow from XXX
allow from XXX
deny from all
</Files>Example:
Password Protect the WordPress Dashboard
This feature can be enabled either manually through the .htaccess, but we recommended using the Directory Privacy feature which you can select from inside of the cPanel.
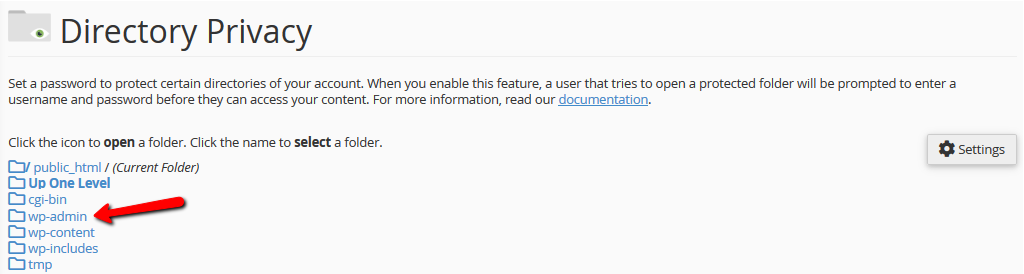
Afterward, go into the folder of your WordPress website, wherever you have it installed and select the /wp-admindirectory, for which you will be creating the authentication page.
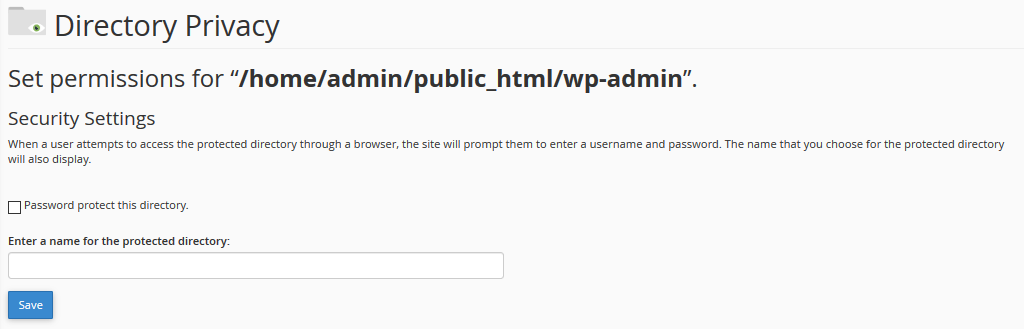
It will then require a SECOND username and password from anyone who is trying to access the admin dashboard, even after a successful initial login.
Cloudflare WAF
Tough luck, you are not getting past that. Applying Cloudflare gives you a lot more features than just its main marketed feature—the CDN function, which makes your website load at top performance all across the earth by having it load up from their closest mirror server depending on the website viewer’s current geographical location, granting it a higher accessibility rate.
For really serious situations where you have noticed a tendency of regular hacking attempts towards your website, we strongly recommend you enable Cloudflare. You do that for it’s WAF feature, which is updated against the newest types of attacks and hacking methods weekly. On the Cloud VPS/Dedicated CPU Server hosting structure, it is possible to access a website via either it’s a domain name or a selected IP address, on Shared Hosting; however it is only possible to access your site via a domain name, giving it one point of entry. With the application of Cloudflare under these conditions, a hacker will only be able to access your website through your WordPress website’s domain. All automated attacks will be blocked within the first 30 seconds if they were able even to start at all.
To Wrap it Up
As a finish to the topic – it’s a paradox, but cybersecurity is as complex as it is simple. Keep your passwords safe, and we will keep your hosting safer. Verify you comply with the steps in this guide and you surely won’t become a victim of a keyboard burglar.

The latest tips and news from the industry straight to your inbox!
Join 30,000+ subscribers for exclusive access to our monthly newsletter with insider cloud, hosting and WordPress tips!


No Comments