
Don’t Be Fooled! Recent Phishing Attacks Targeting cPanel Users
Since April of this year, some hosting providers have reported that their clients are receiving phishing emails via a cPanel impersonator campaign. We did not cover the matter so far, as there were 0 cases in our user base. There was a similar situation back in 2016 during which we did not issue a warning as our users were also not a target. However, we have started receiving reports from our customers in the last few days, which prompted us to publish this warning.
The Deceit
This attack in question makes it seem like the cPanel’s system itself is warning the user about high resource usage that must be resolved. In reality, the ones behind it are phishing for the cPanel account login credentials of the user as they provide a link for the “customer’s convenience”, which leads to a fake login form. More on fake login pages and other phishing methods can be found in our Phishing 101 article.
cPanel has already acknowledged this in an article from the start of 2021, more on which you can read here.
Warning
If you have already provided your username and password via such an URL in an email, please change your password immediately.
Here is how the malicious email looks like:
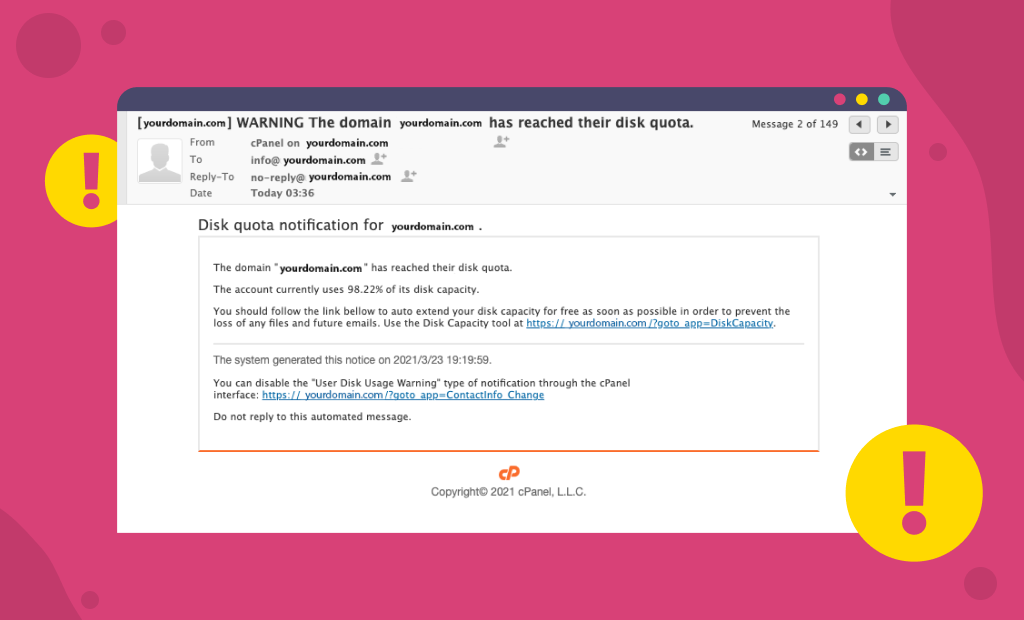
While the current trend is to use the “Disk Quota” other variations with different resource quotas may start circulating in the future.
Analyzing the Email, What to do?
We know advanced users are more likely to check the email header for information about the actual sender, but learning how to check your emails’ legitimacy is very important. This is true even if you are just starting out getting into hosting and the more intricate parts of it.
Most email clients and platforms have extra options for each email which you can access by using the Triple Dot, Cogwheel, and “More” buttons. After that, click on the “Show Original”/”View Source” option to get an “under the hood” look for the actual sender of the email.
Other signs you are being targeted by a phishing campaign:
- Your cPanel username is not mentioned. That is because it is not known by the attackers unless you provide them with it. Instead of that, in the subject and body of the email you will see a domain name. Since you can have many domains associated with the same cPanel and the resources are based per cPanel account and not domain, this is a clear sign something is not right.
- A link to cPanel’s Disk Capacity Tool. As there is no such tool in existence, you can be sure this is as big of a red flag as they come.
- Mentioning the percentage of space taken. In actual cPanel emails the used space is also listed in MB. As the attackers cannot know your hosting plan, and how much space you actually have available and use, they generalize the information via percentages.
Note
Remember that we will never ask you for your cPanel credentials if the account is situated on our own servers. That is due to our Technical team having direct access to all of those accounts.
In the current example, even if you are confident that an email is sent by cPanel, we still advise logging in to your cPanel account on your own without using any of the links in the actual email. You can always login securely in your cPanel by using the appropriate icon on your hosting plan in your FastComet Client Area.
A good security measure that cPanel offers is to activate Two-Factor Authentication, which will prompt you with an extra step during the login process. This is unreplicable by an attacker even if they somehow know your username and password.
From our end, we are actively blocking IP Addresses via which such emails are send towards our customers. However, due to the easy way this IPs can be changed, we can only lower the number of mails, not zero it completely.
You can also contact us anytime you suspect that an email associated with any of the hosting services you use is a phishing/scam attempt just to be on the safe side.

The latest tips and news from the industry straight to your inbox!
Join 30,000+ subscribers for exclusive access to our monthly newsletter with insider cloud, hosting and WordPress tips!


Comments (2)
I got this email just as described. However what keeps me puzzled is that after inspecting the raw source of the email. the sender is an address of my own domain at bluehost. I never created this email address, and yet it is the source address. It is also confirmed to be delivered from a bluehost server.
How can this happen? Bluehost has not offered any explanation about how can this happen.
Hello Cue!
Thank you for the question. Allow us to explain.
The email you received is an attempt at phishing, as you have likely read in our blog post. However, what you are seeing (the email address and its source) is an act of spoofing. Spoofing an email address will do precisely what you are experiencing: the email will look legitimate and sent from a trusted source, when in reality it is not.
Typically an email can get spoofed like that if you have an unprotected form on your website, or if there is an email address in plain view on a page. If that is the case then we recommend securing your form via CAPTCHA and removing any plainly visible email addresses.
We checked to see if your website itself was hosted with us (despite your domain being with Bluehost as you mentioned), since we would have been able to help you with this. However, as that is not the case we cannot provide you with more in-depth assistance.