Preventing DDoS Attacks: Essential Protection Tips
Have you ever felt overwhelmed at work? Everyone in the office demands your attention, your phone is blowing up, your chat windows won’t stop blinking, and your inbox is ceaselessly growing. Most people would struggle immensely to get anything done or just flat-out shut down at that point. Why are we asking you this? Because a similar threat lurks online: Distributed Denial-of-service (DDoS). Nowadays, it is imperative that anyone working with or owning a server or network understands what DDoS protection is.
Many of you have likely at least heard this term. It is one of the “big bads” of the Internet, up there with phishing and malware. Seeing how we have already discussed the other two, it is time to shed some light on what DDoS is, its symptoms, and how to resolve and prevent it. In this blog post, we will examine in detail what DDoS is, its impact, the types of attacks that exist, and how to identify and deal with such an attack. Even if you don’t own or work with servers or networks, you should keep reading: one cannot be too educated about online threats!
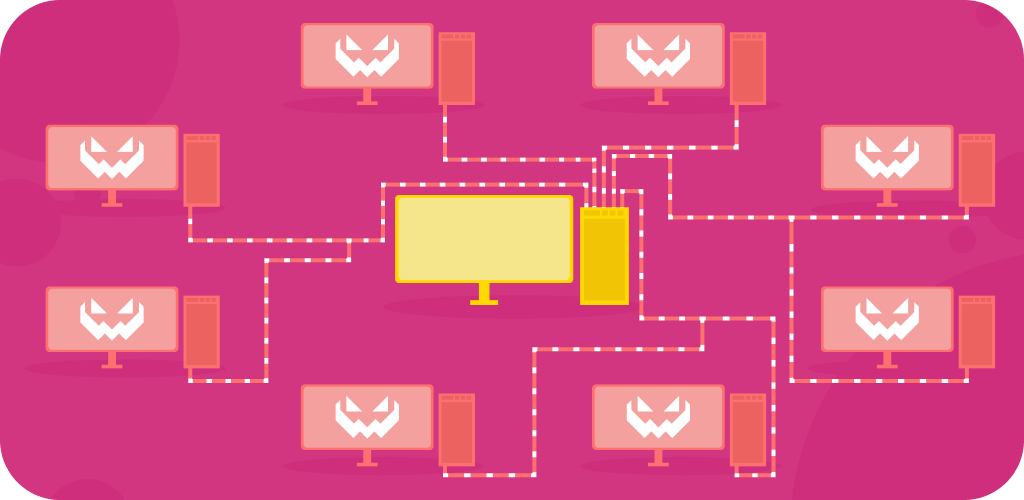
What is a DDoS Attack?
Let us begin with the basics: what is DDoS? The abbreviation stands for Distributed Denial-of-Service. The act of causing such a denial of service is often called a DDoS attack. It targets servers or whole networks to practically halt all of its operations. At its core, a DDoS attack involves flooding a given system or network with requests or data until it can no longer handle the volume and stalls or crashes. Ultimately, this leads to the target losing all ability to function and going offline, which can cause financial and time loss.
The way it works is an attacker, or group of attackers, uses multiple compromised or controlled devices to send a ceaseless stream of requests to a single server or network. Such a group of devices is called a botnet. A controlled or compromised device is usually infected with the malware required for the attack, and the device’s owner might not even know their machine is involved until the attacker triggers the bots. On the other hand, an attacker can forego bots and use a network of tools or devices to achieve the same effect without needing malware. The bottom line is that the target will get overwhelmed and be unable to function properly.
Examples and Impact
Unfortunately, there are countless examples of DDoS attacks since they occur more frequently than anyone would like to admit. The number of attacks has steadily increased over the past half-decade, which is a scary prospect on its own. Still, such attacks typically don’t impact the everyday user on an individual level. It is highly unlikely someone will target your home computer (you are more likely to become a part of a botnet) unless you have some bitter rivals out there. If that is the case, keep reading for our prevention and mitigation advice later.
Typically, DDoS attackers aim at big targets which will produce a more significant impact across the Internet. Why go for Average Joe’s humble laptop over there when you can target Google and really wreak some havoc? And they, the attackers, did try that. Here are some examples of the most famous DDoS attacks.
- Google – In 2020, Google disclosed that in 2017, they were the target of a massive (for the time) DDoS attack. The attack measured at 2.4 Tbps (no, not tablespoons, but Terabytes) and lasted six months. Fortunately for the end users, it seems that nobody noticed. Google did a good job mitigating its effects, considering they managed to keep the news under wraps for three years;
- GitHub – The popular code management service was targeted by a DDoS attack in 2018. It was down for about ten minutes before GitHub’s network protection services were triggered. The attack itself exploited Memcached servers, flooding them with spoofed requests to the sound of 1.3 Tbps;
- Cloudflare, Google, Microsoft, and Amazon – Arguably the most notable DDoS attack of recent times. This one hit the four companies with hundreds of millions of requests per second. The attack was possible due to a vulnerability in the HTTP/2 protocol. The protocol itself is fantastic as it allows for multiple requests over a single connection, but the vulnerability – which has since been resolved – allowed that upside to be abused.
As you can see, despite the severity of the attacks the companies mitigated them and operations returned to normal – or sometimes never even disturbed. DDoS attacks can be diminished, so they are not as scary as they sound at first. However, they can cause significant damage while they last and if not properly taken care of.
When a server or a network is down—no matter the reason—nothing gets done. Workers cannot perform their duties, and users cannot use the provided services. Such outages can cause losses of productivity, money, and—probably most importantly of all—trust and reputation.
Let’s take a web host, for example. If one of their servers is under a DDoS attack, that can cause a cascade of issues.
- Firstly, obviously, the service goes down and customers’ websites stop working. That in itself can cause its own series of issues for the customer. Not only that, but since the support team don’t have access to the server, they cannot resolve any outstanding technical support issues;
- Then, the hosting team has to take measures to stop the attack, which can mean overtime or third-party intervention, meaning monetary loss for the host;
- The other side of the monetary-loss coin is the disgruntled customers who wish to leave the company after their websites were down, which in itself caused them financial losses;
- Finally, after everything is said and done, the host’s reputation and customers’ trust in it will suffer depending on the severity of the issues above.
The final point is probably the worst damage a DDoS attack can cause to a service provider. Customers nowadays rarely go with their gut instinct and instead heavily rely on reviews when making a decision. Such reviews can make or break a business, and we understand why: it is tough to dig yourself out of a negative review hole. Bad reviews equal fewer customers.
Difference Between DoS and DDoS
Before moving on to the different types of DDoS attacks, we wanted to pause for a second and briefly explain the difference between a DoS and a DDoS attack. As you have probably assumed by now, DoS stands for Denial-of-service, and its distributed brother is DDoS. So, in reality, we should clarify what being “distributed” means instead. Fortunately, that is very simple.
During a DDoS attack multiple devices will flood the target with requests to overwhelm it. That we already know. However, during a DoS attack the requests come from a single origin point: a single device . To use a gaming metaphor, DoS is you versus one other player on the enemy team, while DDoS is you versus the entire enemy team.
With this in mind, DoS attacks are much easier to detect and mitigate. There is only one origin point: the volume of requests is smaller, and it takes much longer to ramp up. On the other hand, a DDoS attack comes from multiple devices and, therefore, has more resources at its disposal, so it increases in volume more quickly and can send many more requests. These differences are why we probably never really hear about DoS attacks anymore.
Types of DDoS Attacks
You might have noticed in our examples above that the attacks typically targeted different areas in a system. That is because there are different types of DDoS attacks, each falling into one of three general categories.
- Volumetric
- Application-layer
- Protocol
A volumetric attack is all about raw volume, an application-layer attack exploits weaknesses in an application itself, and a protocol attack abuses IT protocols. Let’s examine each of them individually!
Volumetric Attacks
As the name suggests, the whole point of this attack is to overwhelm the target with numbers. The more data or requests sent to the target, the better (for the attacker, of course). Such an attack aims to occupy the resources of a system or network utterly, and sometimes even both. All their resources are devoted to handling the incoming traffic, leaving nothing left for the rest of the traffic from legitimate users. The “volumetric” umbrella includes a couple of attack types itself.
- UDP – Standing for User Datagram Protocol, UDP is a standard method of transmitting data over the Internet. When compared to some other protocols, UDP is rather primitive. It simply sends data without establishing a two-way connection with the destination. The data packets (unit for data transmission) are simply shoved towards the receiver with no transmission order or check to see if they have arrived. A DDoS attack abusing this protocol overwhelms a UDP port listening for genuine traffic, gobbling up all the server and network’s resources;
- ICMP – The Internet Control Message Protocol is primarily used for error reporting. When two devices connect over the Internet, ICMP will return an error if data does not reach the receiver. However, ICMP is also used for network diagnostics, and the traceroute and ping utilities are both possible because of the protocol. A ping consists of two parts: echo-request and echo-reply. A DDoS attack over ICMP floods the target with echo-requests, forcing it to send echo-replies: this way, it must not only process the requests but also generate replies.
Application-layer
An application-layer DDoS attack is different from what one might consider a “typical” DDoS attack. In this case, an attacker specifically targets vulnerabilities in the application itself. While the focus is not to disrupt the entire server or network infrastructure, the consequences of such an attack can be equally as dire. While, yes, the attack’s primary focus is to disrupt the application itself, the software, that can result in higher resource usage server-side as well. Typically, such attacks happen over HTTP, and there are several types.
- GET – Applications use the GET method to request data. An attack like this can target large files on the website (PDF files, videos, music, etc.) and send countless requests per second for those files;
- POST – Conversely, the POST method sends data to the server. Instead of requesting large files, the attack consists of sending large files to the server, which it has to process one by one;
- Low-and-slow POST – The more subtle and malicious variation of the above attack, this one utilizes the RUDY tool (R U Dead Yet?). The goal is not to flood the website with information but to open many smaller connections and keep them open for as long as possible. Eventually, this consumes all resources available to the website, server, and network.
Protocol
Finally, protocol attacks attempt to abuse Internet protocols to overwhelm a server or network instead of bombarding them with data. Such attacks are typically measured in packets per second. Like the other two categories, several attacks can occur over a protocol.
- SYN Flood – The most common type of protocol DDoS attack, the SYN flood, abuses a specific functionality in the TCP Handshake that happens each time two machines attempt to connect over the Internet. When the handshake occurs, the client sends a SYN packet to the server. The server then acknowledges the connection with a SYN/ACK packet. Finally, the client also returns an ACK packet to the server, and the connection is open. A SYN flood forces the server to keep multiple connections (and ports) open by never returning the client-side ACK packet. If all available ports are occupied, the server will malfunction;
- IP Null – In this type of protocol DDoS attack, the goal is to preoccupy the target with trying to figure out how to handle an unusual connection request packet. Each packet has a header that specifies the connection protocol (TCP, ICMP, etc.), but a hacker can set that to null. That confuses the server, and it has to expend unnecessary resources to determine how to return the packets.
These two are the most prominent protocol DDoS attacks, and combined with the others we discussed in this section, make for an intimidating array. Fear not, though, as there are ways to detect, mitigate, and even prevent such attacks from happening.

Identifying a DDoS Attack
Before fighting a DDoS attack, you must know how to detect it. Sometimes, high traffic can be just that: high traffic. That is why detecting a DDoS attack can be tricky sometimes. Because it is a distributed attack, it often does not come from a single IP and strikes without warning. All it takes is for the hacker to initiate the attack, leaving you to your own devices or their mercy. Sometimes, it could be minutes or hours before anyone notices. However, luckily for everyone on the Internet, there are several red flags to look out for. If you are uncertain if your website or server is under attack, look for these things.
- First and foremost – check how quickly your website loads. Open your website, browse it for several minutes, and observe its behavior. If it is sluggish or gives you errors, something is definitely amiss. Additionally, watch for any other user reports about the website’s performance. If it is happening to other people as well, then it is time to investigate further;
- Next, check your website’s analytics. For example, Google Analytics can show you any spikes in traffic that have occurred recently. Cloudflare can also show you similar data. Typically, you should be able to determine the reason for such spikes, but if the tools you are using can’t do so, then it might be a DDoS attack;
- Thirdly, monitor your server’s connections, its responses to those connections, and the resources it is utilizing;
- During a DDoS attack, its resource usage will steadily climb until it becomes overwhelmed. When that happens, your server will start showing the 503 “Service Unavailable” error due to the shortage;
- You will also see specific IP addresses sending too many connection requests very rapidly;
- Finally, during a DDoS attack, traffic sources can continue querying for data after the TTL for the website has passed. In short, TTL (Time to Live) is a value assigned to DNS records that dictates how long the DNS resolver (typically a user’s ISP) will cache a website’s DNS records. If TTL is 3600 seconds (1 hour), the ISP will cache the website’s DNS records for that long, and any connections made to the website during that time will use the cached IP address instead of querying the DNS server again. When the TTL expires, the ISP refreshes the cache. However, hackers can ignore TTL and continue querying specific data even if TTL has expired. If that is happening, be on the lookout.
You can think of detecting a DDoS attack, like determining if you are ill. Did you randomly sneeze or are you actually getting sick? Treat a DDoS attack the same way: monitor the symptoms before you take hard measures. Sometimes, it can just be increased traffic due to something explainable: an ad campaign, the release of a new viral video, someone famous mentioning your website, etc. Of course, some DDoS attacks are not nearly as subtle and will come in guns blazing to tear down your infrastructure. Those are the easiest to identify, as you can imagine. What do you do? Read on!
Responding to a DDoS Attack
Once you have confirmed a DDoS attack, it is time to take care of it. First and foremost, it is imperative you have a response team trained and ready to react at a moment’s notice. It does not matter whether the team is internal or external. What matters is that they are prepared to handle the situation quickly and effectively. We cannot tell you how to train your team, as that is an extensive topic that will take months to go through. However, we can tell you the general steps our response team takes when we suspect an attack to give you an outline you can refer to.
- Analyze What is Happening – Initially, we keep a close eye on what exactly is occurring. This is a crucial step since the increased traffic might be legitimate;
- Determine the Target – Once we are confident it is a DDoS attack, we pinpoint what it is targeting. Because of the variety of DDoS attacks that exist, they can target different parts of the server, application, or network;
- Identify the Method of Attack – Then, the attack itself. What exactly is it doing? Is it blasting the server ports with requests? Flooding an application? To stop it, you must know what it is doing;
- Implement a Response – Depending on the volume and intensity, you might need only to adjust your server’s firewall if it is a light attack or implement more complex features such as the ones Cloudflare offers;
- Document Everything – Finally, record everything that has happened. Such information is crucial for further analyzing the attack and improving future responses.
We believe these steps are foundational for responding to a DDoS attack. Depending on the complexity of the attack, the actual mitigation strategies will vary.
Mitigation Measures
It is finally time to talk about stopping a DDoS attack. Realistically, the best anyone can do is mitigate it to a point where it does not cause issues since the attack can only be stopped by the one who initiated it. A response team can, at best, moderate and diminish the attack’s impact until it no longer comes from the source. Fortunately, it is possible to do that to such an extent that the attack bothers nobody. With all this said, let’s look at the precise measures to disarm a DDoS attack.
- Rate Limiting – Rate limiting is the most fundamental thing one can do to disrupt a DDoS attack. It is a great first step because it – as the name suggests – limits the times a connection can repeat an action within a specific time frame. Generally, a rate limiter tracks how often a given IP makes requests and prevents them from doing so if they exceed the threshold. Since a limiter runs within an application, the steps to enable it will vary depending on what you are using. As an example, Wordfence for WordPress has a rate-limiting option;
- Traffic Filtering and Blocking – After identifying the malicious IPs, you can block them via your server’s firewall or router. Always be careful when doing this, as you do not wish to block legitimate IPs. If you notice that the IPs are all from the same region of the world, you can also use the more nuclear option of blocking that entire region. Again, depending on the system you use, how you do these things will vary. At FastComet, we use WHM and cPanel, and they both offer IP blocking and regional restrictions;
- Load Balancing – If you have the capability, you can spread the load across multiple duplicate servers or backup servers. Load balancing will ensure that the impact from the DDoS attack does not overwhelm a single server and is instead diffused across multiple resources to lessen it;
- Inform Your ISP – Your ISP can actually help you in the event of a DDoS attack. They can block or filter malicious traffic before it reaches your server or network. Some ISPs even provide DDoS scrubbing services; however, we recommend not relying solely on your ISP. Their primary concern is not to protect their customers from DDoS;
- Prioritize – If essential services or software must remain online, you can prioritize them over non-essential ones. You can deactivate those so that the rest can utilize the freed resources.
By taking these measures, you can limit or completely diminish the effects of a DDoS attack. Additionally, you can also implement third-party DDoS protection services in your measures.
DDoS Protection Services and Cloudflare
Most of what we described above you can do server-side. However, you can further bolster your defenses by using one of the many online DDoS protection services: Cloudflare, Bunny, Azure, Vercara, etc. We recommend using the free Cloudflare plan since it offers many services and features (DDoS protection included). Nonetheless, you should consult your own team and research the perfect solution for your needs. There might be something better for you out there. While we are on the topic, let’s take a look at precisely what Cloudflare has that can shield your server and network from DDoS attacks. Of course, you must be using their services already, and you can check out our tutorial about that if you would like to start.
Firstly, they have a super handy “Under attack” mode that you can turn on with the flick of a switch. Simply log into your account, open the domain that is under attack, and enable “Under attack” in the Overview tab.
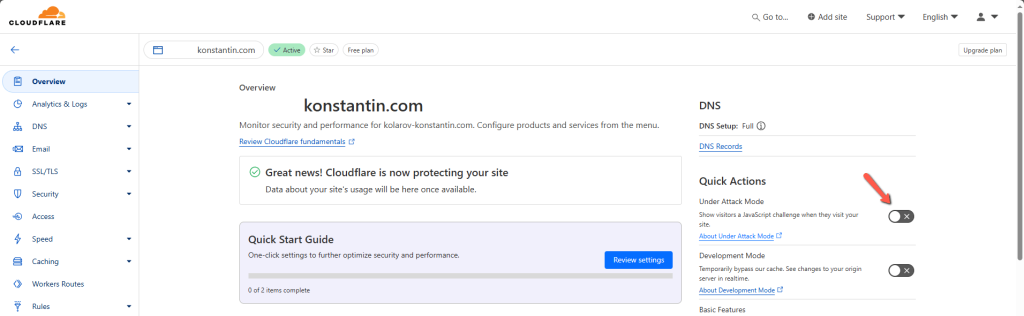
This mode works for application-layer attacks and implements additional security checks to ensure that only legitimate traffic goes through. It issues a JavaScript challenge that most bots cannot resolve. Any typical, legitimate browser is has a JavaScript stack and will pass the challenge on its own. On the other hand, bots don’t usually have such a stack, so they cannot handle the challenge and are, therefore, prevented from establishing a connection. You might already be familiar with what the page looks like.
Cloudflare also offers a highly customizable WAF (Web Application Firewall). Within it, you can create a wide variety of rules that will help mitigate a DDoS attack. For example, you can make a rule to block all traffic from a specific host or IP or create rate-limiting rules. On top of that, Cloudflare offers a preset of DDoS protection rules that are available to all their users and constantly protect your website from an attack. These rules are also customizable; you can find them and the WAF in the Security section of your Cloudflare dashboard.
We strongly recommend you read Cloudflare’s documentation and consider it if you want to use a third-party DDoS protection service. With the functionalities it offers, you can quickly enable the ones you need and adapt them to the attack. The upside of Cloudflare is that it comes with many other benefits, which will also help improve your website’s performance.
But what about preventing attacks from happening entirely? We cannot promise that is possible, but there are some preventative measures to reduce the chance of them happening.
Preventative Measures
As mentioned above, we do not want to promise you that any of what we describe now is a surefire way to shield your server or network from a DDoS attack. However, these measures can greatly reduce the chance of an attack succeeding, improve your response and recovery times, or both.
Firstly, as mentioned earlier, have a well-educated and trained team on standby. It can be your system administrators, a separate set of people, an external security company, or whatever else you are comfortable with. What matters is that the people handling the situation know what they are doing. Cyber security is no joke nowadays, and your team should keep on top of the latest security practices, be knowledgeable in DDoS mitigation techniques, and be aware of how your server and network infrastructure work.
Have them collaborate with your ISP to determine if they can help in any way with DDoS and safeguarding against it. Additionally, either the same team or a different one (we recommend the same team) should have a recovery plan in place in case the DDoS attack causes more damage than anticipated. Back up all important system data regularly and ensure you have the means to restore it in an emergency.
Next is online security itself. The online community considers several practices to be “the best” when it comes to online security, and you should follow all of them.
- Updates – Do not allow any of your software to become outdated. Outdated software has glaring vulnerabilities that hackers can exploit. Updates patch those vulnerabilities, making your software more secure. For example, we have an entire blog post devoted to why you should always keep your WordPress installation up to date. You can apply almost everything said there to other applications and software as well;
- Use a CDN – CDNs do more than just help users connect to your website quickly from around the globe. Nowadays, respectable CDNs offer complete suites of security features, as we mentioned in the previous section. Using a CDN can significantly bolster not just your DDoS prevention measures but the overall security of your website;
- Authentication and Authorization – Strong, unique passwords can be a hassle, but they are essential nowadays. Implement password policies that demand strong, complex passwords that must be renewed at regular intervals. Also, ensure that users and processes have the minimum level of access to perform their functions;
- Redundancies – Ensure that your infrastructure does not have a single point of failure. If possible, use multiple data centers and have a high bandwidth roof to ensure it can handle spikes in traffic;
- Firewalls – We would be surprised if people on the Internet do not know what a firewall is. WAF or otherwise, your server or network will not survive nowadays without one;
- SSL Certificates – While not directly connected to DDoS prevention, we must include it here because 11% of websites online still don’t use one. That is a lot of websites, considering there are 1.13 billion of them. Install an SSL certificate, it is not difficult. It will encrypt traffic, help your WAF and CDN with picking out malicious requests, and just makes your website more secure as a whole.
The bottom line is to strive to have your network, server, and websites as secure as possible, educate yourself and your team about DDoS, and you should be as safe as possible in this Wild West we call the Internet. There is an additional benefit to all of this, though: all of this should also boost the performance of your website and server. SEO loves security and quickness, so the additional bandwidth and CDN can boost your rankings a bit, too. The more resources your server has to work with – or the more data centers the load is spread over – the more responsive and unburdened it will be.
You Are Ready
As you can see, a DDoS attack is scary, but with the right preparation, it is possible to mitigate its effects to nothing. It is an expense, we know, but cyber security is something companies should not shirk nowadays. You should definitely work within your budget and be as ready as you can be. The upside is that millions of other websites and companies are on the Internet, so we hope you never have to deploy what we have described in this blog post. Do not slack on security, though!

The latest tips and news from the industry straight to your inbox!
Join 30,000+ subscribers for exclusive access to our monthly newsletter with insider cloud, hosting and WordPress tips!


No Comments