How to opt-in for Preload List
Updated on Apr 30, 2018
Even if you have the HSTS header added to your website's .htaccess file, there is still a small window of vulnerability for newly installed browsers or completely wiped local states. To counter this, the Chromium Projects came up with the idea to create a preload list for chrome which contains all domains (and subdomains/nested subdomains) that were opt-in by their owners to be HSTS enabled by default. Mozilla Firefox and Safari maintain similar lists based on the original Chrome list to be able to do the same. You can opt-in for inclusion in this list if you can cover the requirements predefined by the Chromium Projects team:
- Serve a valid certificate.
- Redirect from HTTP to HTTPS on the same host, if you are listening on port 80.
- Serve all subdomains over HTTPS.
- In particular, you must support HTTPS for the www subdomain if a DNS record for that subdomain exists.
Additionaly, to serve the HSTS header on the base domain for HTTPS requests requires:
- The max-age must be at least 31536000 seconds (1 year).
- The includeSubDomains directive must be specified.
- The preload directive must be specified.
- If you are serving an additional redirect from your HTTPS site, that redirect must still have the HSTS header (rather than the page it redirects to).
To address these requirements in order:
- Serving a valid certificate can be easily achieved by issuing a Let's Encrypt certificate for your domain and subdomains or by using a GlobalSign or other SSL certificate of your own. Check out our Let's Encrypt announcement blog post for more information on how to issue a certificate and our other blog post regarding Let's Encrypt Wildcard certificates.
- Redirecting from HTTP to HTTPS on the same host can be done by adding this to your .htaccess file and making sure you change "yourdomainhere.com" with your actual domain:
RewriteEngine On RewriteCond %{SERVER_PORT} 80 RewriteRule ^(.*)$ https://yourdomainhere.com/$1 [R=301,L]
- Let's Encrypt will allow you to choose the subdomains which you want to cover when issuing a certificate for a certain domain. Just make sure your subdomains don't have any mixed content issues.
- You will need the HSTS header for making the correct HTTPS replies. For more information on the header, please visit our How to Enable HSTS tutorial on the matter.
Once you cover all of the above, go to this page for a check on HSTS compliance. Enter your domain, and you should see the following screen.
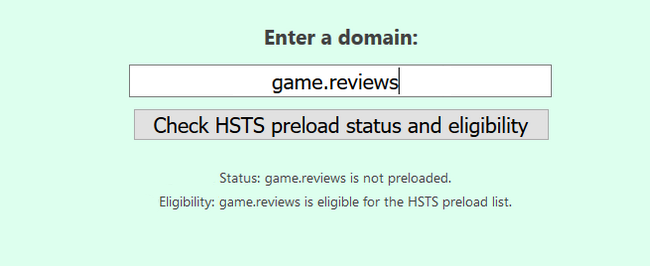
Warning
Once added to the preload list, the reversal of this action is very time consuming and may take up to 12 weeks for Chrome users and more for the rest of the browsers. For more information on this, please visit our "How to opt-out of the Chrome Preload List" tutorial.
Below it, you will have the submit form in which you have to agree with the two terms by checking their boxes and then click on the submit button.
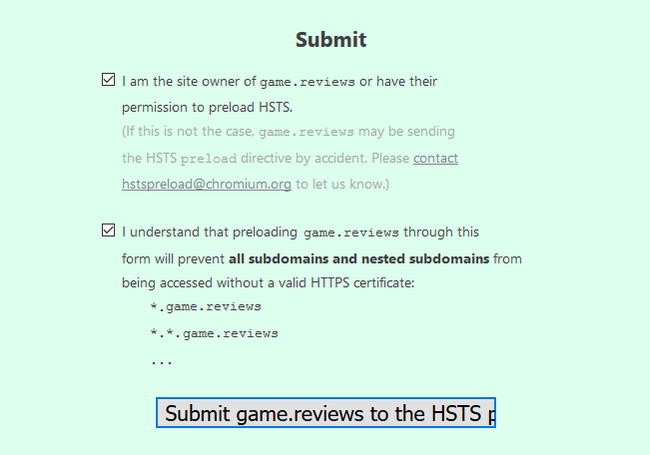
With this, your domain is now in the preload list, and will directly load via HTTPS mitigating MITM attack attempts.

High Security Hosting
- Network Firewall
- Web Application Firewall
- Brute-force Protection
- Exploits and Malware Protect
- CageFS Security
- ModSecurity Manager