How to activate the free Cloudflare SSL
Updated on Oct 1, 2024
In this section of our Cloudflare tutorial, we will discuss the SSL options Cloudflare offers its customers. An SSL certificate is a security layer that encrypts the connection between a client (your browser) and the website's hosting server. That ensures no data is transmitted via plain text, making it far less likely to be intercepted and stolen by a malicious party. Such encryption is mandatory nowadays, not just for security but also for SEO. Your website will not rank highly if you do not have an SSL certificate installed. Fortunately, Cloudflare issues one for free to all websites connected to it. Additionally, you can install one very easily with our services! Check out our tutorial for more information.
That said, though, you might be asking yourself why Cloudflare needs to issue an SSL certificate if you already installed one on your website. That is a good question, so read on, and we will explain! The first section is the Overview tab within the SSL/TLS section, where all of Cloudflare's SSL options and settings are located.
This post includes:
Overview
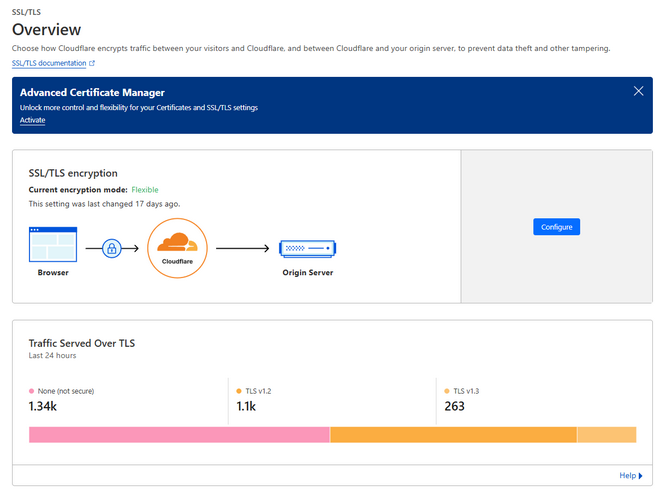
When you click on SSL/TLS, you will be taken to the Overview tab, which is one of the most vital pages in the SSL/TLS section of Cloudflare. From here, you have direct control over how the connection to your website is encrypted. Additionally, this page also shows what traffic, in terms of encryption, has passed through our website for the last twenty-four hours.
This is a vital page because from the Configure button, you can change how the connection between a browser and your website is encrypted. This is also where the answer to the earlier question lies: Why does Cloudflare need to issue an SSL certificate if your website already has one? That is actually very easy to explain, and the diagram above visualizes it well.
Without Cloudflare, there are two points between a browser and a website: the browser and the website's server. Simply put, the browser sends a connection request to the server, to which the server responds with the necessary page. However, when you add Cloudflare to this, the points become three. To provide all its benefits, Cloudflare's servers stand between the browser and the website's origin server. The connection goes through Cloudflare's servers, and Cloudflare does what it needs to do. Then, the connection continues to your server.
Since the connection is, for all intents and purposes, split in two by Cloudflare, the SSL certificate you have on your website only encrypts the connection between Cloudflare and your website's server. If Cloudflare was not present, the entire connection would be encrypted. That is why Cloudflare needs to issue its own SSL certificate to encrypt the connection between the client (browser) and their servers. And with all of this said, this is where the Overview tab's main functionality comes into play. Click Configure, which will take you to the Configure Encryption Mode page.
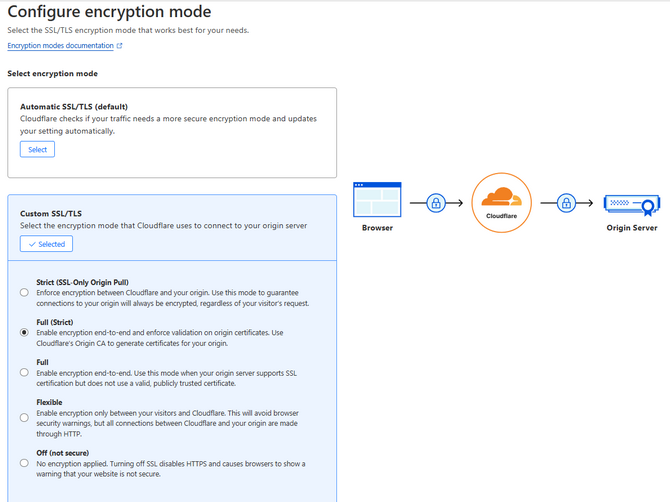
Here, you can set how you want Cloudflare to handle connections between itself and your visitor and between itself and your server. Each has an explanation, but allow us to simplify it.
- Automatic SSL/TLS - This setting automatically adjusts the level of security of your encryption based on your traffic. It is good if you have to change the encryption mode often;
- Strict (SSL-Only Origin Pull) - This is the most secure encryption mode; however, it is only available for customers on the Enterprise plan. It ensures that the connection between the visitor and your origin server is encrypted through and through. That applies even if the connection from the visitor is over HTTP and, therefore, not encrypted;
- Full (Strict) - The Full (Strict) is the most secure encryption mode free users have access to, but even it is more than enough. This mode allows both HTTPS and HTTP connections between the visitor and Cloudflare and Cloudflare and the origin server, depending on which protocol the visitor uses. Additionally, this mode enforces strict requirements for SSL certificates on the origin server;
- The certificate must be valid and not expired;
- A publicly trusted Certificate Authority must issue it;
- And must contain a Common Name or Subject Alternative Name that matches the targeted hostname (origin server);
- Full - This encryption mode works like the Full (Strict) one but lacks the SSL certificate requirements. Use it if your origin server cannot cover them;
- Flexible - If you use this option, the connections to your website will only be partially secure. Cloudflare will allow HTTPS connections from visitors, but they will be made over HTTP towards your origin server. Using this mode is not recommended, and you should only select it if your server is incapable of supporting SSL certificates;
- Off (Not Secure) - Finally, this mode will actually turn all HTTPS requests into HTTP ones, therefore sending all data between the visitor and your server via unencrypted plaintext. We do not recommend you use this mode unless there are some specific conditions that require it.
Finally, depending on your individual SSL setup, your website might experience redirect loops or mixed content errors after adding it to Cloudflare. Often, that can be easily fixed by selecting one of these modes (typically one of the Full ones).
Edge Certificates
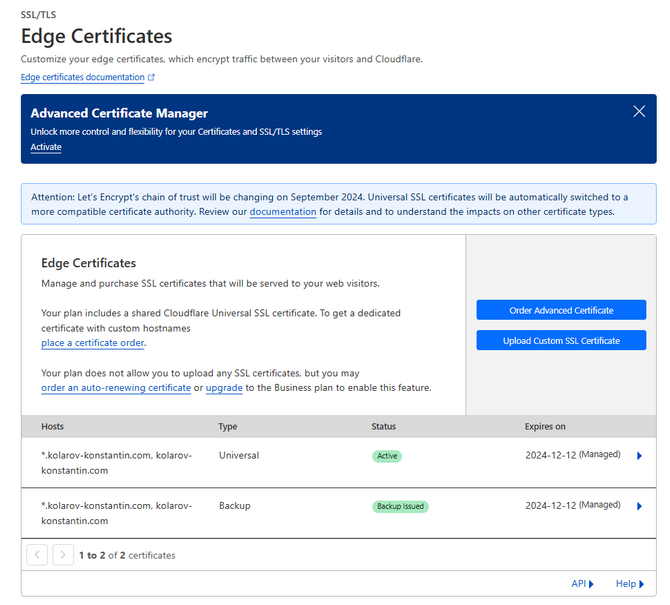
The next tab in the SSL/TLS section is Edge Certificates. Here you can see the Universal SSL certificate that is shared among the websites on your Cloudflare account. The term Edge Certificate means an SSL certificate on Cloudflare's Edge servers: that is what they call their global network of servers. Therefore, an Edge Certificate is one that encrypts the connection between a visitor and an Edge server.
The table shows the domains currently secured by the certificate. If you click the arrows next to them, you will find further information. Below the table are several additional options you can toggle.
- Advanced Certificate Manager - Unavailable to free users, this manager allows users more granular control over their SSL certificates and TLS settings. It offers the ability to create and upload additional SSL certificates that Cloudflare does not issue. It also allows users to customize the hostname that appears on the certificate or configure its validity and Subject Alternative Name. Total TLS is also part of the manager, which will issue individual certificates for every domain on the account;
- Always Use HTTPS - As the name suggests, this setting will redirect all HTTP requests to HTTPS;
- HSTS - HTTP Strict Transport Security (HSTS) is a security feature that ensures browsers always connect to a website via HTTPS, even if you try to access it over HTTP instead. It forces the browser to connect to the website via HTTPS, remember that setting, and always use it. You can enable it for your websites if necessary with the toggle;
- Minimum TLS Version - Here, you can set the minimum TLS version visitors must have to be able to access your website;
- Opportunistic Encryption - This toggle allows browsers to benefit from the improved performance of HTTP/2. However, the connection will remain unencrypted if they are connecting insecurely;
- TLS 1.3 - Toggle this if you want Cloudflare to use the latest TLS version for improved security and performance;
- Automatic HTTPS Rewrites - Enable this option if you want Cloudflare to help fix mixed content. This will change the resources or links for your website's content from "http" to "https" if possible;
- Disable Universl SSL - Finally, you can remove any currently active Universal SSL certificates from your domains. This will also prevent the automatic renewing and ordering of said certificates.
Typically, we recommend leaving the default settings as they are. However, you should look through them yourself and adjust them according to your website's specific needs.
Client and Origin Certificates
In addition to offering a Universal Certificate for all your domains, Cloudflare can also create Client and Origin certificates. You can find them in their respective sections under SSL/TLS.
Such certificates are used to protect different parts of the connection between a user and your website.
- Client Certificate - A certificate like this is used to verify the identity and, therefore, the security of a client (user, device, application, etc.) to a server. It primarily confirms that the client is trusted and authorized to access the server. Such a certificate is useful if you wish to validate your application as secure and safe to let through Cloudflare's defenses;
- Origin Certificate - On the other hand, this type of certificate is used to secure the connection between Cloudflare and your origin server; therefore, the name. These certificates are specifically designed for use with Cloudflare and are part of how Cloudflare helps protect and optimize your website. Such a certificate is installed on your origin server, which assures Cloudflare that it is encrypted and secure.
As you can see, these are just two more options that Cloudflare offers as a part of a complete SSL suite. Chances are, if you are using a reputable hosting service like FastComet, you will not need to issue such certificates. However, it is always good to have the option in case it becomes necessary and you need some quick and easy certificates.

CDN Hosting
- Free Domain Transfer
- 24/7 Technical Support
- Fast SSD Storage
- Hack-free Protection
- Free Script Installation
- Free Website Transfer
- Free Cloudflare CDN
- Immediate Activation